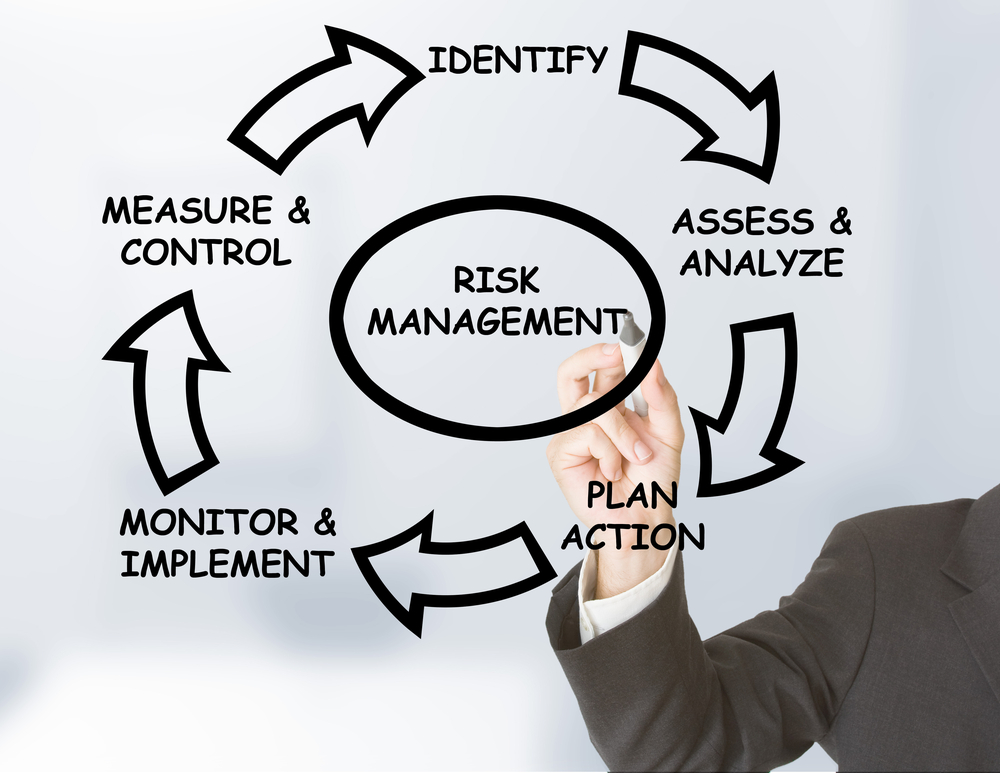
TPRM Explained Third Party Risk Management (TPRM), is the process of analysing and minimising risks associated with outsourcing third-party vendors or service suppliers.
There is a wide range of digital risks that fall under the third-party risk category. These risks could be financial, reputational and security.
Vendors have access to sensitive data, intellectual property, and protected health information (PHI) which can create risks. Third-Party Risk Management (TPRM) is essential to all Cybersecurity programs. This is because third-party relationships are crucial for business operations.
Definitions of Third Party
Any entity with which your company works is a third-party. This includes suppliers, manufacturers and service providers as well as affiliates, distributors, retailers, agents, and resellers. They may be either upstream (suppliers or vendors) or downstream (distributors, resellers, and agents), and they can also include non-contractual entities. They could, for example, offer a SaaS product to keep your employees productive and provide transportation for your physical supply chains.
What is the difference between a third-party and a fourth-party?
Third-parties are suppliers, vendors, partners, or any other entity that does business with your organization directly. A fourth-party, however, is the third party of your third-party. Fourth-parties, or “Nth parties”, are relationships that exist in deeper parts of the supply chain and are not contractually connected to your organization.
What is Third-Party risk management?
Because third-party risks can have a direct or indirect impact on your cybersecurity, it is crucial to manage them. Third-party risk management can increase complexity in your information security because it is often more cost-effective to have an expert in a particular field outsource the work. You don’t have full transparency into third-party security controls and they are not usually under your control. While some vendors have strong security standards and sound risk management practices, others are less so. Every third-party can be a target for a cyber attack or data breach. Vendors with vulnerable attack surfaces could gain access to your company. Your attack surface will increase the more vendors you have and the greater the risk of being attacked.
The regulatory and reputational impact of inept third-party risk management plan has been greatly increased by the introduction of data protection laws and data breach notification laws such as GDPR, CCPA and FIPA. If a third party has access to customer information, your organization could face regulatory penalties and fines, even if they weren’t directly responsible. This is a famous example: Target’s HVAC contractor led to the exposure millions of credit card numbers.
Our complete guide to third-party risk management.
What are the risks posed by third-parties?
Organizations can face many risks when they work with third parties, including:
Cybersecurity Risk: This is the risk that an organization could be exposed to loss or damage due to a cyberattack or security breach or other security incidents. Due diligence is a key factor in reducing cybersecurity risk. This includes monitoring the vendor’s lifecycle and constant monitoring. Operational risk is the risk that a third party could disrupt business operations. These risks are typically managed by contractually bound service levels agreements (SLAs), business continuity plans, and incident response plans. You may choose to have a backup vendor depending on the vendor’s criticality. This is a common practice in financial services.
Compliance, legal, and regulatory risk: A third-party could impact your compliance with agreements, legislation, and regulations in your area. This is especially important for government agencies, financial services, and healthcare.
Reputational Risk: A third-party’s risk of causing negative public opinion. Poor recommendations, poor customer service, and dissatisfied customers are just a few of the many problems. Third-party data breaches, such as Target’s 2013 data breach, are the most dangerous.
Financial Risk: There is a chance that third-party data breaches could have a negative impact on your financial success. Poor supply chain management could mean that your company is unable to sell new products.
Strategic Risk: There is a risk that your company will not be able to achieve its business goals due to the involvement of a third party vendor.
Reasons to Invest in Third Party Risk Management
The following are reasons you should consider investing in third-party risks management
Savings: Third-party risk management framework can be viewed as an investment. While it will cost you time and money upfront, it can save you money in the long-term. A data breach that involves third-parties costs an average of $4.29 million. A third-party risk management strategy that is effective can significantly reduce the likelihood of data breaches. Regulatory compliance: Third party management is a key component of many regulatory requirements, such as FISMA and SOX, HITECH or CPS 234, GLBA or the NIST Cybersecurity Framework. Depending on the industry you work in and what type of data (e.g. You may be required to evaluate your third-party ecosystem in order to avoid being held responsible for security incidents. Third-party risk management has become a standard industry practice in many sectors. Non-compliance is not an option.
Reduced risk: Due diligence speeds up vendor onboarding and lowers third-party security breaches. Vendors must be reviewed throughout their entire lifecycle, as new security threats can be introduced.
Confidence and knowledge: Third-party Risk Management increases your visibility and knowledge of third-party vendors and improves decision making at all stages, including the initial assessment and offboarding.
What’s a Vendor Management policy? What is a Vendor Management Policy? It identifies the vendors that are most at risk and sets out controls to reduce third-party or fourth-party risk.
These could include ensuring that vendor contracts have a minimum security rating and implementing annual inspections or replacing existing vendors with vendors who meet security standards. This may give a brief overview of your third-party risk management processes and frameworks. Many vendors have a poor record of managing their customers’ and their data. This is despite having invested heavily in internal security measures. To learn more, read our guide on creating a vendor management policy.
SpartanTec, Inc. Wilmington NC can assist with treat analysis from third-party risks. Our team can help make sure that you company is safe from various kinds of threats.
How To Evaluate Third-Parties
There is a variety of methods and solutions for evaluating third parties. The board and senior management will generally decide which methods are most appropriate for them. This depends on the industry and number of vendors they use and their information security policies. Security ratings, security questionnaires and penetration testing are all common solutions.
Call SpartanTec, Inc. now if you need more information about third-party risk management
SpartanTec, Inc.
Wilmington, NC 28412
(910) 218-9255
http://manageditserviceswilmington.com
Serving: Myrtle Beach, North Myrtle Beach, Columbia, Wilmington, Fayetteville, Florence

No comments:
Post a Comment