The Risk Management Framework (RMF), a set criteria, outlines how IT systems in the United States must be designed, secured, and managed.
The original RMF was created by the (DoD) and applied by the rest of US federal IT systems in 2010. The National Institute of Standards and Technology (NIST), which maintains NIST, provides a solid foundation to any data security strategy.
The RMF is a combination of several existing risk management frameworks. It also includes several systems and processes. To identify cyber risks, it requires firms to implement secure data governance systems.
What is the Risk Management Framework?
Although the general concept of risk management and the framework for risk management may seem similar, it is important to distinguish the differences. NIST has provided detailed information on the risk management process in several of its subsidiary frameworks.
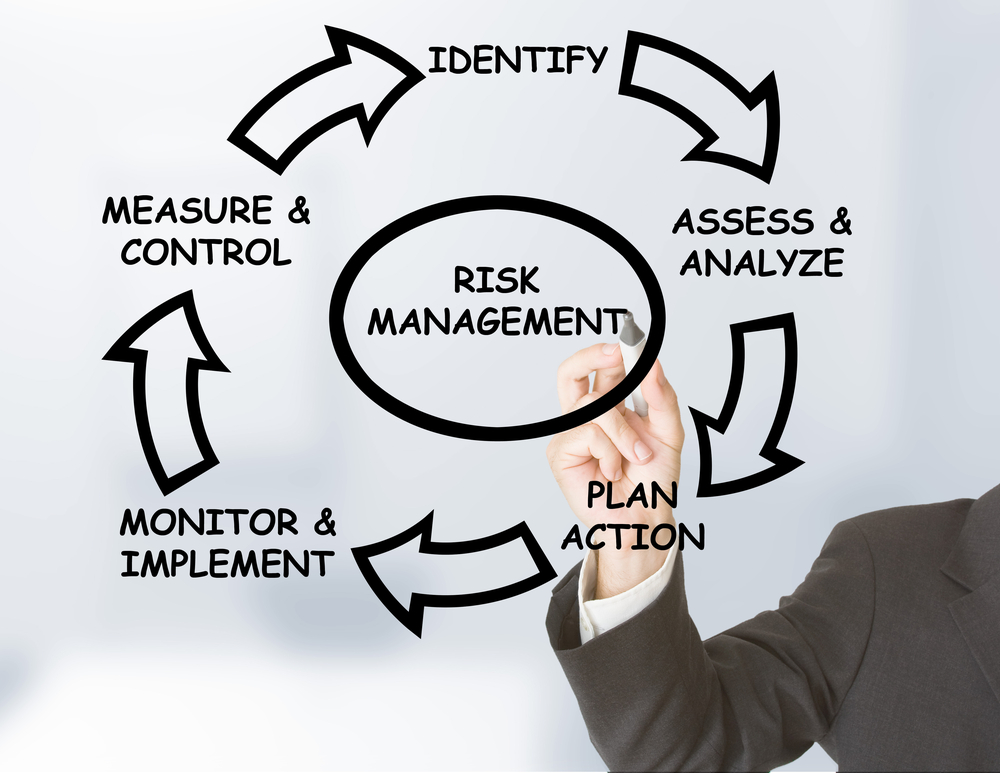
The 5 components of risk management
It can be helpful to break down the different risk management requirements when you get started with the RMF. These categories can be used to help you create a risk management plan that will work, from identifying your most important risks to how you will reduce them.
Risk Identification
Risk identification is the first and most important part of the RMF. According to NIST, the most common risk factors are threat, vulnerability and impact, likelihood, and predisposing conditions. This step will allow you to brainstorm all possible risks that you can see across your systems, as well as make sure that they are on top of the list in terms of the priorities them through different factors.
Threats are events that could cause harm to the organization through intrusion, destruction or disclosure.
Vulnerabilities refer to weaknesses in IT security, procedures, controls, and systems that could be exploited or manipulated by external or internal bad actors.
The measure of the extent to which an organization will be affected by a vulnerability or threat.
Probability is a measure of risk factor that takes into account the likelihood of an attack on a particular vulnerability.
Predisposing circumstances are any factor within an organization that can increase or decrease the likelihood of vulnerability.
Risk Assessment and Measurement
After identifying the threats, vulnerabilities and impact of each condition, you can then calculate and rank the risks that your company must address.
Risk Mitigation
The organization can use the previous ranked list to determine how to mitigate threats from the most severe to the mildest. The organization may decide that the risks below the level of the ranked list are not worth addressing. This could be because the threat is unlikely to get exploited or because there are too many more serious threats that can be managed immediately.
Risk reporting and monitoring
The RMF mandates that organizations keep a list and monitor all known risks to ensure compliance with policies. According to statistics, many companies fail to report successful attacks that they have been exposed to. This could affect their peers.
Risk Governance
All of the above steps should be codified into an organizational risk management system.
What Can A Business Benefit From An Effective Risk Management Framework?
Although the RMF is required for US Government-owned businesses, any company can benefit from implementing a risk management program. Working towards RMF compliance means creating a data- and asset governance system that provides full-spectrum protection against cyber threats.
A company will reap the benefits of a well-designed risk management system. Asset Protection
A good risk management system will help you understand the risks your business is facing and take the necessary steps in order to protect your assets. A comprehensive risk management system will help protect your data as well as your assets.
Reputation Management
Modern business practices require reputation management. Limiting the negative consequences of cyberattacks is an integral part in protecting your reputation. The importance of data privacy is becoming more apparent to Americans, and not only because the US privacy laws have become increasingly strict. Data breaches can damage your company’s reputation. A solid risk management system can quickly help companies identify gaps in enterprise-level controls, and create a plan to minimize or eliminate reputational risks.
The Risk Management Framework (RMF), a set criteria, outlines how IT systems in the United States government must be designed, secured, and monitored.
The original RMF was made by the (DoD) and used by the other US federal information systems in 2010. The National Institute of Standards and Technology (NIST), which maintains NIST, provides a solid foundation to any data security strategy.
Download the free Essential Guide to US Data Protection Compliance and Regulations. The RMF is a combination of several existing framework of risk management. It also includes many independent systems and processes. To identify cyber risks, it requires firms to implement secure and safe data governance systems.
This guide will cover everything you need to know regarding the RMF. The components of the framework will be broken down in several sections.
What is the Risk Management Framework?
Although the general concept of risk management and the framework for risk management may seem similar, it is important to distinguish the differences. NIST has provided detailed information on the risk management process in several of its subsidiary frameworks.
The most important document is “NIST SP 800-37 Rev. 1”, which describes the RMF as a six-step process to design and engineer data security processes for new IT systems. It also suggests best practices and procedures that federal agencies must follow when enabling new systems.
The RMF includes the SP 800-37 primary document. It also uses the SP 800-53, SP 80053A, SP 800-53A and SP 800-137 supplemental documents:
NIST SP 800-30 entitled Guide for Conducting risk assessments provides an overview of risk management and describes how to conduct them.
NIST SP 800-37 is a discussion of the risk management framework and includes much of what we’ll be covering in the rest of this guide.
NIST SP 800-39, entitled Managing Information Security Risk
, outlines the multi-tiered approach to risk management that is essential for compliance with the RMF.
The 5 components of the risk management framework
The components of the risk management framework
It can be helpful to break down the RMF’s risk management requirements into separate categories when you get started. These categories can be used to help you create a risk management plan that will rwork, from identifying your most important risks to how you will reduce them.
Risk Identification
Risk identification is the first and most important part of the RMF. According to NIST, the most common risk factors are threat, vulnerability and impact, likelihood, and predisposing conditions. This step will allow you to brainstorm all possible risks that you can see across your systems, as well as prioritize them with the use of different factors.
Threats are events that could cause harm to the organization through intrusion, destruction or disclosure.
Vulnerabilities refer to weaknesses in IT security, procedures, controls, and systems that could be exploited or manipulated by external or internal bad actors.
The measure of the extent to which an organization will be affected by a vulnerability or threat.
Probability is a measure of risk factor that takes into account the likelihood of an attack on a particular vulnerability.
Predisposing circumstances are any factor within an organization that can increase or decrease the likelihood of vulnerability.
Risk Assessment and Measurement
After identifying the threats, vulnerabilities and impact of each condition, you can then calculate and rank the risks that your company must address.
Risk Mitigation
The organization can use the previous ranked list to determine how to mitigate threats from the most severe to the mildest. The organization may decide that the risks below the level of the ranked list are not worth addressing. This could be because the threat is unlikely to get exploited or because there are too many more serious threats that can be managed immediately.
Risk reporting and monitoring
The RMF mandates that organizations keep a list and monitor all known risks to ensure compliance with policies. According to statistics, many companies fail to report successful attacks that they have been exposed to. This could affect their peers.
Risk Governance
All of the above steps should be codified into an organizational risk management system.
The 6 Risk Management Framework (RMF), Steps
The risk management framework steps
RMF is a broad concept that requires companies to identify the system and data risks they are vulnerable to and to take reasonable steps to reduce them. These objectives are broken down into six separate but interrelated stages in the RMF.
Categorize Information Systems
NIST standards are used to categorize information systems and provide accurate risk assessments.
NIST will tell you which systems and information to include.
Based on the categorization, what level of security should you implement?
FIPS Publication 299, Standards for Security Categorization Federal Information and Information Systems. Special Publication 800-60 Rev. 1 (Volume 1, Vol. 2), Guide for Mapping Types Information and Information Systems to Security Categorie. Select Security Controls
To “facilitate an easier, consistent, comparable and repeatable method of selecting and specifying security control for systems,” select the appropriate security controls from NIST publication 800-53.
Refer to Special Publication 800-53 Security and privacy Controls for Federal Information Systems and Organizations, ed. Note that the updated version 80053 will take effect on September 23, 2021. Keep checking back for more details.
Implement Security Controls
You should now put the controls that you have chosen in the previous step. Document all processes and procedures necessary to keep them in operation.
Multiple publications offer best practices for security controls implementation. You can search this page for these best practices.
Security Controls
You can reduce the risk to your business and data by ensuring that security controls are in place.
Authorize Information Systems
Are security controls in place to minimize risk for the organization? If so, then that control is authorized! Congratulations!
Refer to Special Publication 800-37 Rev. 2 Risk Management Framework for Information Systems and Organizations: Security and Privacy Approaches for the System Life Cycle
Monitoring Security Controls
Continuously monitor, assess and adjust security controls to improve their effectiveness. Notify your designated officials of any security control changes.
Refer to Special Publication 800-37 Rev. 2 Risk Management Framework For Information Systems and Organizations: An System Life Cycle Approach to Security and Privacy
What Can A Business Benefit From An Effective Risk Management Framework?
Although the RMF is required for US Government-owned businesses, any company can benefit from implementing a risk management program. Working towards RMF compliance means creating a data- and asset governance system that provides full-spectrum protection against cyber threats.
A company will reap the benefits of a well-designed risk management system. Asset Protection
A good risk management system will help you understand the risks your business is facing and take the necessary steps in order to protect your business assets. A comprehensive risk management system will help protect your data as well as your assets.
Reputation Management
Modern business practices require reputation management. Limiting the negative consequences of cyberattacks is an integral part in protecting your reputation. The importance of data privacy is becoming more apparent to Americans, and not only because the US privacy laws have become increasingly strict. Data breaches can damage your company’s reputation. A solid risk management system can quickly help companies identify gaps in enterprise-level controls, and create a plan to minimize or eliminate reputational risks.
IP Protection
Every company has intellectual property. A risk management framework is required for this property. Intellectual Property theft can occur if you offer, distribute, sell, or provide a product, service, or other activity that could give you an advantage. The risk management framework protects against possible losses of competitive advantage, business opportunities, as well as legal risks.
Competitor Analysis
The fundamental operation of your company can be improved by creating a risk management plan. You can gain a competitive edge by identifying the risks you face and taking steps to mitigate them.
How can SpartanTec, Inc. help you with risk management?
Identify sensitive and at-risk data and systems (including permissions, users, folders, etc.).
Manage access and protect that data;
Monitoring and identifying suspicious activity or unusual file activity can help you identify and monitor what’s going on with that data.
Data integrity should be the primary focus of any RMF process. This is because data security threats are most likely to be the most important for your business. SpartanTec, Inc. can conduct a comprehensive risk assessment of your company.
Call SpartanTec, Inc. now if you want to know more about risk management.
SpartanTec, Inc.
Wilmington, NC 28412
(910) 218-9255
http://manageditserviceswilmington.com

 “They will pursue mom-and-pops, and may only get $3,000 to $5,000, but that’s the way it all started. Kennedy stated that ransomware was started by grandma and grandpa hacking infrastructure.
“They will pursue mom-and-pops, and may only get $3,000 to $5,000, but that’s the way it all started. Kennedy stated that ransomware was started by grandma and grandpa hacking infrastructure.